Why Penetration Testing Matters: Reduce Breach Risk & Accelerate Enterprise Deals
Enterprise buyers demand proof of security. Learn how penetration testing reduces breach risk, strengthens compliance reports, and helps you close bigger deals faster.
Penetration testing is a proactive security practice designed to uncover vulnerabilities before malicious attackers can exploit them. In this post, we’ll break down what penetration testing entails, how it’s performed, and why it’s a crucial component of any comprehensive security strategy. For further insights, visit our blog on SoftwareSecured.
Definition and Purpose
At its core, penetration testing is a simulated cyberattack on your systems, networks, or applications. Its primary goal is to identify security weaknesses that could be exploited by real-world attackers. Unlike a general vulnerability assessment, penetration testing actively exploits vulnerabilities in a controlled manner to demonstrate their potential impact.
Flavours of Penetration Testing
Penetration tests can be tailored to suit different scenarios and attack perspectives. Common testing approaches include:

- Black Box Testing: Testers operate with no prior knowledge of the system, simulating an external attacker.
- White Box Testing: Testers have full insight into the network and application details, allowing for a comprehensive evaluation.
- Grey Box Testing: This method provides testers with limited information, striking a balance between real-world conditions and informed testing.
These flavours, which mimic various attack scenarios, help organizations understand how different threat actors might approach their systems. More about our approach can be found on our services page.
Types of Penetration Testing
Beyond the testing approaches, penetration testing is often categorized by the target environment. Key types include:
- External Network Penetration Testing: Focuses on systems and services exposed to the internet.
- Internal Network Penetration Testing: Simulates an insider threat by assessing the security of systems within an organization’s internal network.
- Web Application Pentesting: Evaluates web applications for vulnerabilities such as SQL injection or cross-site scripting.
- Mobile Pentesting: Examines mobile applications on various platforms to uncover security issues unique to mobile environments.
- Hardware Pentesting: Targets physical devices and embedded systems to discover vulnerabilities in hardware components.
- IoT Pentesting: Assesses Internet of Things devices, which often face security challenges due to limited resources and outdated software.
- Protocol Pentesting: Focuses on the security of communication protocols, ensuring data integrity and confidentiality.
- Wireless Pentesting: Evaluates wireless networks for vulnerabilities that might permit unauthorized access.
- Physical Pentesting: Simulates real-world physical intrusion attempts to test the effectiveness of security controls.
Methodology and Process
A structured methodology is crucial for an effective penetration test. The typical process involves:
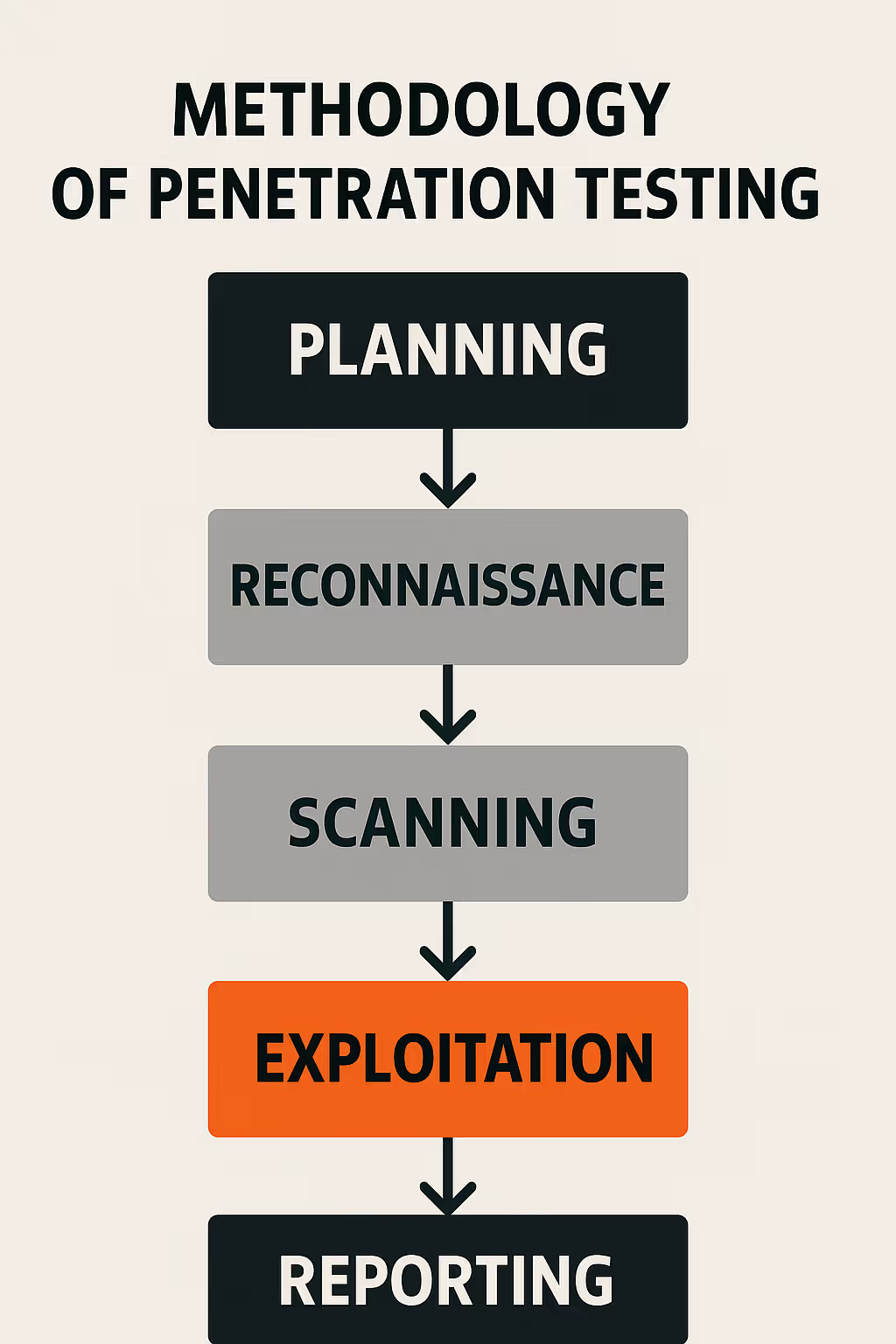
- Planning and Scoping: Defining the test’s scope—including systems, applications, and boundaries—while ensuring you have explicit authorization.
- Reconnaissance: Gathering intelligence about the target to identify potential vulnerabilities.
- Scanning: Using automated tools and manual techniques to detect open ports, services, and weak spots.
- Exploitation: Actively attempting to exploit identified vulnerabilities to assess their impact.
- Post-Exploitation: Evaluating the extent of access and potential damage following a breach.
- Reporting: Documenting findings, risk levels, and recommendations for remediation.
Each step provides actionable insights that help organizations improve their security posture. More details on our testing process are available on our process page.
Tools and Techniques
Penetration testers rely on a blend of industry-standard tools and expert manual techniques. Some common tools include:
- Network Scanners: Tools like Nmap are used to map network infrastructure.
- Exploitation Frameworks: Metasploit provides a robust environment for testing vulnerabilities.
- Web Application Testing Suites: Burp Suite assists in identifying and exploiting web vulnerabilities.
While automated tools streamline testing, manual techniques are essential for discovering complex vulnerabilities. For an overview of the tools we use, explore our services.
Legal and Ethical Considerations
Given the intrusive nature of penetration testing, adhering to legal and ethical guidelines is paramount:
- Authorization: Secure explicit, written permission before initiating any tests.
- Rules of Engagement: Clearly define the boundaries and guidelines for the test.
- Ethical Standards: Ensure all testing practices comply with legal standards and ethical guidelines to prevent unintended harm.
Benefits and Limitations
Benefits:
- Risk Identification: Penetration testing uncovers vulnerabilities that might otherwise remain hidden.
- Proactive Security Posture: Organizations can address issues before they are exploited by attackers.
- Regulatory Compliance: Regular testing is often required to meet industry standards and regulations.
Limitations:
- Scope Constraints: Time and scope limitations may prevent every vulnerability from being identified.
- Dynamic Threat Landscape: New vulnerabilities and attack methods continually emerge.
- Resource Intensive: Comprehensive testing requires time and specialized expertise.
Understanding these factors helps organizations set realistic expectations and continuously improve their security measures. For further insights on our testing benefits, visit our blog.
Real-World Examples and Case Studies
Real-world case studies highlight how effective penetration testing can uncover critical vulnerabilities and drive strategic improvements. Below are a few examples of real-world case studies:
- Financial Services Security Enhancement:
A major financial services firm underwent both external and internal penetration testing. The tests revealed vulnerabilities in legacy systems and misconfigured services that could have exposed sensitive financial data. Remediation steps taken significantly bolstered their security posture.
Read how Trust & Will was able to use penetration testing to close their security gaps.
- Healthcare Data Protection:
In another case, a healthcare organization was tested to assess its web applications and network configurations. The penetration testing process identified vulnerabilities that could have compromised patient information. The ensuing remediation efforts helped the organization enhance its data protection protocols and comply with industry regulations.
Discover how BlyByrd avoided costly HIPAA violations by leveraging penetration testing.
- E-commerce Application Fortification:
An e-commerce business faced challenges in securing its online platform and mobile applications. Comprehensive testing uncovered issues like flaws in session management and data handling. Addressing these vulnerabilities not only fortified the platform but also increased customer trust by demonstrating a commitment to security.
Learn more ThriveCart leveraged comprehensive penetration testing including business logic testing to avoid fraud.
For additional examples and success stories, browse through our extensive case studies library.
Conclusion and Best Practices
In today’s rapidly evolving threat landscape, regular penetration testing is not just an optional extra—it’s a strategic necessity. By simulating real-world attacks, organizations can identify vulnerabilities, improve their security posture, and better prepare for potential threats.
Best Practices Include:
- Regular Testing: Schedule regular penetration tests and conduct additional tests after significant system changes.
- Comprehensive Scope: Ensure testing covers all critical assets, including networks, applications, and user practices.
- Continuous Improvement: Use test findings to continually update and refine security policies and defenses.

.avif)



