3 Types of Cross-site Scripting Attacks & 4 Mitigation Strategies
Understanding the three main types of XSS attacks can help you plan to mitigate them using one of these four recommended strategies.
Cross-site scripting (XSS) is an application security vulnerability that allows a hacker to inject malicious code into a website or mobile application. XSS flaws have been known and studied since the 2000s. Understanding the different types of XSS attacks is crucial as these flaws have been known and studied since the 2000s. Despite their popularity and plague, they are still frequently found and do not show signs of disappearing anytime soon. The impact of an XSS attack can be an important finding in penetration testing. XSS attacks occur when a malicious user enters a piece of code as input data. The malicious code is eventually interpreted as DOM markup and runs on a victim’s browser. With their code running on the victim’s browser, the attacker can steal confidential information and perform other actions in the context of that user, also bypassing numerous security controls like the same-origin policy.
Three Common Types of XSS Attacks
Stored XSS Attack Explanation
Stored XSS is when the malicious script is injected into a vulnerable app where it is persisted or stored on the vulnerable page of the application. When a victim loads the affected page in the application the malicious script will execute the context of a user’s session. Here is an example of stored XSS in the Elementor Page Builder tool.
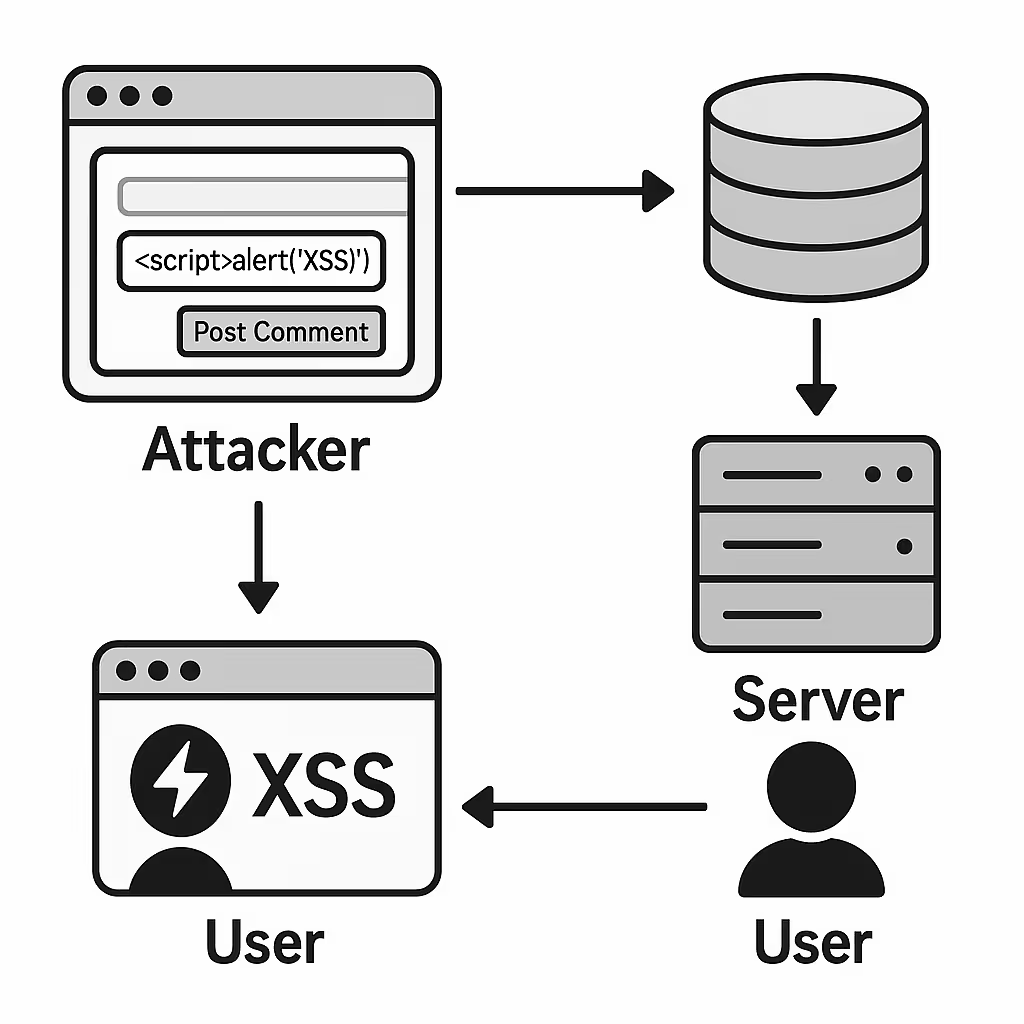
Reflected XSS Attack Overview
Reflected XSS attacks occur when a victim is tricked by the attacker into visiting a malicious link within the vulnerable application. The malicious link may be introduced to the victim via social engineering, phishing, or watering hole-style attacks. In this scenario, these non-persistent scripts are injected into a user’s browser session and executed as a direct reflection within HTTP responses returned by the server. Here is an example of reflected XSS in the JetBrains TeamCity tool.

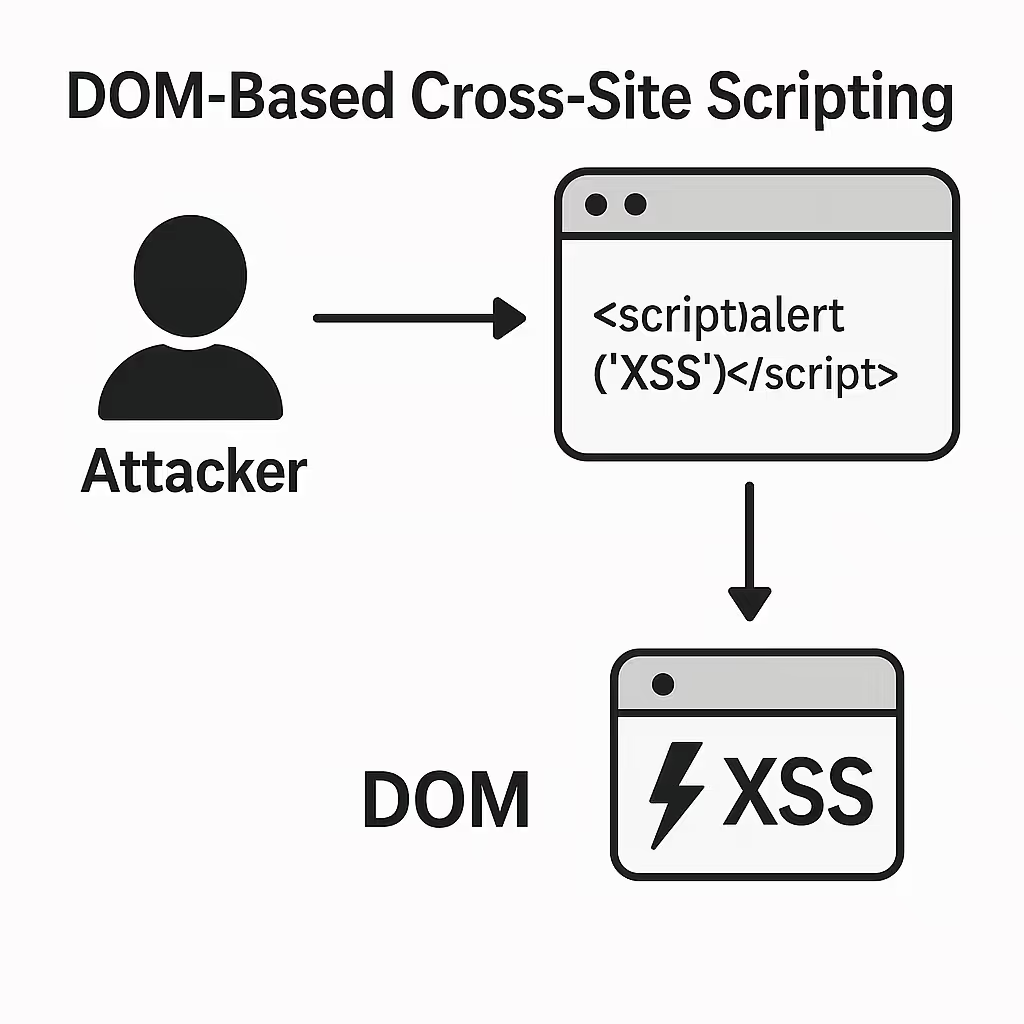
Understanding DOM-Based XSS Attacks
DOM-based XSS also involves a malicious link and may be introduced to the victim in a similar attack vector as reflected XSS, although unlike what we’ve seen so far DOM-based XSS attacks do not require interaction with a server. The attacker’s code is stored and executed in the browser. Thus, securing our server-side code will offer no protection against DOM-based attacks. The attack’s independence from the server also makes detection more complex.
Exploring the Growing Popularity of XSS Issues
Actions an attacker can take when their code is running on a user’s browser include:
- Steal the user’s sensitive information, such as login credentials, credit card information, and other private/sensitive data.
- Hijack a user’s session (if your application allows JavaScript to read HTTP session information).
- Send and receive data from a malicious web server.
- Access the user’s webcam, microphone, and location through HTML 5 APIs or other known browser vulnerabilities.
- Advanced phishing techniques that will be difficult for both non-technical and technical users to identify.
The presence of XSS vulnerabilities depends on various factors, and these factors explain why such flaws are still being found at an increasing rate. Not all developers are necessarily trained in the risks associated with XSS and the impact of these vulnerabilities is sometimes not perceived correctly. As systemic security starts with the code, developers lack the knowledge and frameworks to integrate and manage many security elements. When a site or an application is coded without a framework, it is, unfortunately, easy to write code that is vulnerable to XSS and to overlook the verifications and controls of the data received.
Effective Strategies for Mitigating XSS Attacks
No single technique will solve XSS. However, using the right combination of defensive techniques is necessary to prevent XSS. There are various ways to try and protect yourself and your organization from this class of vulnerability, and we will go into various prevention methods.
1- Implementing Framework Security Measures
Fewer XSS bugs appear in applications built with modern web frameworks. These frameworks steer developers towards good security practices and help mitigate XSS by using templating, auto-escaping, and more. Understand how your framework prevents XSS and where it has gaps. There will be times when you need to do something outside the protection provided by your framework. This is where Output Encoding and HTML Sanitization are critical. OWASP is producing framework-specific cheat sheets for React, Vue, and Angular.
2- Adopting a Proactive XSS Defense Philosophy
For XSS attacks to be successful, an attacker needs to insert and execute malicious content in a webpage. Each variable in a web application needs to be protected. Ensuring that all variables go through validation and are then escaped or sanitized is known as perfect injection resistance. Any variable that does not go through this process is a potential weakness. Frameworks make it easy to ensure variables are correctly validated and escaped or sanitized.
However, frameworks aren't perfect and security gaps still exist in popular frameworks like React and Angular. Output Encoding and HTML Sanitization help address those gaps.
3- Leveraging Output Encoding Techniques
Output encoding is recommended when you need to safely display data exactly as a user typed it in. Variables should not be interpreted as code instead of text. This section covers each form of output encoding, where to use it, and where to avoid using dynamic variables entirely.
Start with using your framework’s default output encoding protection when you wish to display data as the user typed it in. Automatic encoding and escaping functions are built into most frameworks.
If you’re not using a framework or need to cover gaps in the framework then you should use an output encoding library. Each variable used in the user interface should be passed through an output encoding function. A list of output encoding libraries is included in the appendix.
There are many different output encoding methods because browsers parse HTML, JS, URLs, and CSS differently. Understanding the various types of XSS attacks is crucial when selecting the appropriate output encoding method. Using the wrong encoding method may introduce weaknesses or harm the functionality of your application.
4- Importance of HTML Sanitization in XSS Prevention
Sometimes users need to author HTML. One scenario would be to allow users to change the styling or structure of content inside a WYSIWYG editor. Output encoding here will prevent XSS, but it will break the intended functionality of the application. The styling will not be rendered. In these cases, HTML Sanitization should be used.
To learn more about XSS protection and specific output coding code snippets, visit OWASP’s XSS Cheat Sheet.
Conclusion
In summary, mastering the three XSS variants—Stored, Reflected, and DOM-based—is the first step toward robust web application security. By combining framework-provided protections with rigorous output encoding and targeted HTML sanitization, you establish multiple layers of defense that greatly reduce the attack surface. Embrace a “perfect injection resistance” mindset: validate every input, escape or encode every output, and sanitize any user-authored HTML. Finally, augment your development controls with regular security reviews or a professional penetration test to catch any gaps before they reach production. With these practices in place, you’ll be positioned not just to defend against today’s XSS threats, but to stay ahead of tomorrow’s.

.avif)



