Common Security Misconfiguration Habits
Learn about common security misconfiguration habits, how hackers leverage these habits, and how to prevent these attacks.
Even the most advanced security systems can be rendered useless by a single misconfiguration, leaving organizations vulnerable to devastating attacks. These seemingly innocent mistakes can have far-reaching consequences, providing malicious actors with the foothold they need to compromise systems, steal sensitive data, or disrupt critical operations. From gaping holes in access controls to ill-configured cloud environments and everything in between, security misconfigurations can result in catastrophic incidents. Common security misconfiguration habits, such as weak access controls, can result in catastrophic incidents.
As per a report by Titania, network misconfigurations alone cost organizations 9% of total annual revenue! But don’t worry, I also have some good news! By identifying the cause and following some secure practices, you can minimize the risks of security misconfigurations. In this blog we will delve deep into the common security misconfiguration habits, shedding light on their root causes, examining real-world examples, and most importantly, effective strategies to avoid them. But before anything else, let’s understand what security misconfigurations are.
What are security misconfigurations?
Security misconfigurations refer to incorrect or insecure configuration settings in software, systems, or networks. They arise from errors in design, deployment, or ongoing maintenance processes. These misconfigurations can occur at various levels of an organization's technology stack or digital infrastructure including but not limited to:
- Operating System: Misconfigured OS settings can lead to vulnerabilities such as insecure open ports, improper user permissions, or ineffective security controls, providing potential entry points for attackers.
- Web Application: Web applications often have complex configurations involving web servers, databases, and application frameworks. Misconfigurations in these components can expose sensitive data, enable unauthorized access, or facilitate a variety of different application-based attacks, such as injection attacks.
- Network: Errors such as misconfigured firewalls, routers, or access control lists can result in unintended network access, leaving systems and data exposed to malicious actors.
- Database: Improperly configured database servers can introduce risks such as weak authentication mechanisms, improper permissions, or unencrypted data storage.
- Cloud Service: Misconfigurations in cloud resources, such as storage buckets, virtual machines, or access control policies can lead to denial of service, resource exhaustion, subdomain takeover, unauthorized access, or the exposure of sensitive information.
- Application Framework: Misconfigured application frameworks or libraries can introduce vulnerabilities, such as enabling debug mode in production environments, improper error handling, or inadequate input validation.
Each security misconfiguration serves as an open invitation for attackers, expanding the organization's attack surface. Attackers are constantly on the lookout for low-hanging fruit, and security misconfigurations are a prime example.
Security misconfigurations can lead to data breaches that result in reputational and financial losses. Loss of business, recovery expenses, and fines for data breaches can be very expensive for organizations. That's a significant chunk of resources that could have been better utilized elsewhere. Let’s go one step further and understand the impact of security misconfigurations in depth.
Impact of security misconfigurations
Security misconfiguration is at number 5 on the latest OWASP Top 10 and it has held its place in the top 10 since 2010. It indicates how security misconfigurations have been a grave threat to organizations for over a decade. As decision-makers, it's crucial to understand the impact it can have on your organization. let's delve into the consequences of security misconfigurations and why they demand your immediate attention.
1- Financial losses
Have you thought about the aftermath of a breach due to security misconfigurations? A whirlwind of expenses, including loss of revenue, incident response, legal battles, regulatory fines, and potentially even customer compensation. It's like a never-ending shopping spree at the expense of your organization's hard-earned cash. According to a study by IBM, the average cost of a data breach is a staggering $4.35 million! I’m sure no organization would like to lose millions due to a breach.
2- Reputational damage
Every decision you make when it comes to cybersecurity puts your reputation on the line. Your reputation is a valuable asset, and security misconfigurations can swiftly tarnish it. A breach caused by a misconfiguration can erode customer trust, damaging your brand's reputation and credibility. News of a security incident spreads like wildfire in the age of social media, potentially leading to customer attrition, and a long and costly journey to rebuild trust. Reputational damage is not something that will go away as soon as you’re clear of the breach. It will take years to rebuild the reputation and a huge amount of resources.
3- Operational disruptions
Misconfigurations can disrupt your day-to-day operations, resulting in downtime, service interruptions, and productivity losses. Your operations grind to a halt, leaving employees twiddling their thumbs, and customers scratching their heads. Every minute of system unavailability can translate into lost revenue, missed deadlines, and dissatisfied customers. This impacts multiple departments, affecting your organization's efficiency and morale.
4- Regulatory compliance issues
In today's tightly regulated security landscape, compliance is paramount. A misconfiguration misstep can land you in a tangled mess. Security misconfigurations can expose your organization to compliance violations, leading to hefty fines, legal actions, and damaged relationships with regulatory bodies. It's vital to maintain a robust security posture and ensure your systems align with industry standards and data protection regulations
5- Opportunity costs
The cost of exploitation of security misconfigurations goes beyond dollars; it's about lost opportunities. Rather than investing time, effort, and finances into growth and innovation, you find yourself stuck in reactive mode, addressing preventable security incidents. This opportunity cost can hinder your organization's ability to stay competitive and agile in a rapidly evolving landscape.
Now that we have explored the impact of security misconfigurations and their potential consequences, here are some examples of real-life incidents due to security misconfigurations:
- A misconfigured app exposed the personal details of NASA employees, including names, email addresses, and project information. The issue occurred due to the wrong permissions assigned for visibility options.
- A security misconfiguration in the United States Department of Defense’s server leaked internal U.S. military emails. The misconfiguration left the server without a password, allowing anyone access to the sensitive mailbox data.
You can read about more real-life incidents at the following links:
Understanding the true impact of security misconfigurations is the first step toward proactive defence. By doing so, you can ensure a secure environment for your employees and customers. Security misconfigurations can be catastrophic, but why do they occur in the first place?
Common security misconfiguration habits: Why do misconfigurations happen?
Security misconfigurations often stem from some common habits. Understanding the underlying reasons behind them is crucial to tackling them. By exploring common security misconfiguration habits, we can gain valuable insights and take proactive steps to bolster our security defences.
1- Debugging enabled
One of the most prevalent misconfiguration habits is leaving debugging features enabled in production environments. While these tools are valuable during the development and testing phases, their presence in live systems can disclose sensitive information, such as stack traces and debugging messages to potential attackers. It is crucial to ensure that debugging functionality is disabled or properly secured in production environments.
2- Default credentials
Another common misconfiguration arises from the use of default or weak credentials for various system components such as databases, network devices, or application interfaces. It's like handing out keys without bothering to change the locks. Failing to change default usernames and passwords creates a significantly easy entry point for attackers to gain unauthorized access to sensitive resources. Always change default credentials and enforce strong password policies to mitigate this risk. No offence, but leaving default credentials is a sign of irresponsibility and it should be avoided.
3- Misconfigured permissions
Improperly configured permissions can lead to unauthorized access or privilege escalation within a system. This includes granting mismanaging access controls or overlooking the principle of least privilege. The NASA incident we looked at earlier is an example of misconfigured permissions. Regularly review and fine-tune permission settings to ensure that only authorized individuals have access to sensitive data and functionalities. Create secure processes to invoke and revoke permissions as needed.
4- Default error page or example page
Neglecting to customize default settings, such as error pages or example pages, can provide valuable information to attackers. It is like offering attackers a treasure map to your system Default error pages may inadvertently disclose sensitive system details or expose directory structures, while example pages may reveal implementation details that can aid attackers in crafting targeted exploits. Customize default settings and remove unnecessary examples to minimize the risk of information leakage.
5- Cloud misconfiguration
With the growing adoption of cloud services, misconfigurations in cloud environments have become a more prevalent concern. From poorly configured security groups to lax access control lists and failure to implement encryption, the cloud can become a playground for cyber mayhem. Ensure robust configuration and compliance management for cloud resources, and leverage security tools and best practices provided by cloud service providers.
6- Hardware misconfiguration
Misconfigurations don't discriminate, they are not limited to software systems alone but also extend to hardware components. Hardware components such as routers, firewalls, or intrusion detection systems can be misconfigured, leaving gaps in your network security posture. Even the latest and most advanced machines can fall to the ground due to misconfigurations. It is essential to follow vendor guidelines, and industry best practices, and conduct regular audits to identify and rectify any misconfigurations in hardware devices.
By being aware of these common habits that cause security misconfigurations, organizations can proactively address potential vulnerabilities and enhance their overall security posture. As we’ve now understood the impact of and common reasons for security misconfigurations, let’s understand how attackers use misconfigurations to their benefit by looking into some real-life examples.
How can attackers leverage common security misconfigurations?
It is important to understand attackers' thoughts and attack processes to effectively mitigate security misconfiguration-related risks. Therefore we will look into 3 real-life examples of security misconfigurations and how attackers can exploit them.
1- Use of default credentials/weak passwords
This misconfiguration involves leaving the default administrator credentials enabled when installing a system and using easily guessable passwords. As per an analysis, 75% of the world's top websites allow weak passwords. This is a common oversight that many website administrators make when setting up a site. We will take an example of a popular content management system (CMS) – WordPress as 43% of all the websites on the internet use WordPress.
Impact
Once attackers exploit this misconfiguration and gain access, they can manipulate the website, inject malicious code, deface it, or even install malware that infects visitors' devices. Attackers may further exploit the compromised WordPress site by leveraging its reputation to distribute malware, launch phishing campaigns, or propagate attacks on visitors of the site.
Attack process
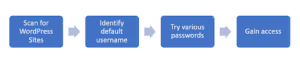
- Attackers scan the internet for websites running WordPress and specifically target those that still have the default "admin" username.
- Attackers use automated tools and various techniques, such as using common/default passwords, dictionary attacks, or leveraging leaked password databases, to guess the password associated with the "admin" username.
- Once the attackers successfully guess the password, they gain full administrator access to the WordPress site. This gives them control over the entire website and its content.
2- Improper access control
When configuring an S3 bucket, it is essential to ensure that access permissions and ACLs are set correctly to prevent unauthorized access. Here we discuss the improper access control settings of an Amazon S3 bucket.
Impact
Attackers can gain unauthorized access to the bucket and its contents, leaving sensitive data exposed, and allowing attackers to modify or delete stored information. A compromised bucket can be used as a launching pad for further attacks, such as hosting malicious files, distributing malware, or launching phishing campaigns.
Attack process
- Attackers employ various reconnaissance techniques and tools such as "S3Scanner" or "Bucket Stream" to identify publicly accessible S3 buckets or those with improper access control configurations.
- Attackers try to perform different actions and try to guess the access permissions and ACL rules.
- If the bucket is set to allow public access or has incorrectly defined ACLs, attackers can access the bucket's contents. They leverage the AWS Command-Line Interface (CLI) or API calls to interact with the bucket programmatically.
- With access to the compromised bucket, attackers can download, modify, or delete files within it using tools like "AWS S3 sync" or AWS S3 cp commands.
- The stolen data can be further exploited for identity theft, unauthorized account access, or targeted phishing attacks.
3- Use of default configurations
Here we discuss a vulnerability in Apache Superset, tracked as CVE-2023-27524, that allowed unauthorized users to access sensitive data due to a misconfiguration in the application's authentication mechanism. When a user logs in, a session cookie containing their user identifier is sent to their web browser. This cookie is signed with a SECRET_KEY, which should be randomly generated and securely stored. However, due to a misconfiguration, the application defaulted to a publicly known secret key:
SECRET_KEY = '\2\1thisismyscretkey\1\2\e\y\y\h'
This allowed attackers to generate and sign cookies, effectively authenticating as the app administrator.
Impact
Exploiting this misconfiguration could enable attackers to bypass authentication and gain unauthorized access to sensitive information within Apache Superset. Depending on the privileges associated with the compromised account, the attacker could view, modify, or exfiltrate confidential data.
Attack process

- Attackers scan for systems running Apache Superset and investigate the authentication mechanisms in use.
- Attackers with no prior privileges generate and sign their cookies using the SECRET_KEY.
- Attackers set the forged session cookie in the browser’s local storage and access the application as legitimate users.
- Attackers can log in as an administrator by forging a session cookie with a user_id or _user_id value set to 1 because in most cases the first user is the administrator.
- Attackers can then query, modify, and delete any data in the database as well as execute remote code on the database server.
These are some real-life examples of security misconfigurations and how attackers exploit them. We seem to have covered enough ground on common security misconfiguration habits and how they can be exploited. Now let’s discuss some steps you can take to prevent security misconfigurations in your environment.
Identifying and avoiding common security misconfiguration habits
In our ongoing quest to enhance cybersecurity practices, it is imperative to address the common security misconfiguration habits and occurrences. Here are some approaches you can use to identify and avoid misconfigurations.
1- Asset inventory
Maintaining a comprehensive asset inventory is crucial for managing security misconfigurations. Start by identifying all assets within your organization's network, including servers, databases, applications, and network devices. Keep the inventory up to date by regularly scanning and tracking changes in your environment. This enables you to have a clear understanding of your assets and facilitates targeted configuration management.
2- Leverage secure configuration templates and guidelines
Utilize automated configuration management tools and frameworks that provide secure configuration templates and guidelines. These tools can help you enforce consistent and secure configurations across your infrastructure, reducing the risk of misconfigurations caused by human error.
3- Automatic detection for misconfigurations
Leveraging automated tools and solutions can significantly streamline the detection of security misconfigurations. Implement robust configuration scanning tools that can identify misconfigurations across your infrastructure. These tools can analyze configurations, compare them against industry best practices, and provide detailed reports on any deviations.
4- Penetration testing
Conducting regular penetration tests is a proactive approach to uncovering misconfigurations that could be exploited by adversaries. Engage with experienced penetration testers who can simulate real-world attack scenarios and identify vulnerabilities in your systems. By performing targeted assessments, they can pinpoint misconfigurations and provide actionable recommendations to mitigate risks.
Not sure how to choose a penetration testing service? Read this article to help you decide. Or talk to us to get high-quality Penetration Testing as a Service (PTaaS)
4- Continuous monitoring and auditing
Establishing a robust system for continuous monitoring and auditing is essential to maintain the integrity of your configurations. Implement logging mechanisms that capture and analyze security-relevant events across your infrastructure. This allows you to detect any unauthorized changes, track configuration drift, and respond promptly to potential misconfigurations. Regularly review audit logs to identify patterns or anomalies that may indicate misconfigurations or malicious activities.
Best practices and frameworks
We don’t need to start from scratch when it comes to combating common security misconfiguration habits. There are several frameworks available that we can refer to and tweak as per our needs.
1- Center for Internet Security (CIS) benchmarks
The CIS provides comprehensive security configuration guidelines for various systems, platforms, and software applications. These benchmarks offer detailed recommendations and controls to help organizations secure their infrastructure, network devices, operating systems, and cloud environments. By aligning your configurations with the CIS benchmarks, you can enhance your security posture and reduce the risk of misconfigurations.
2- NIST Cybersecurity Framework
The NIST Cybersecurity Framework provides a risk-based approach to managing and improving cybersecurity posture. While it doesn't specifically focus on configuration management, it includes guidelines and recommendations for secure configurations as part of its broader framework. NIST has developed a series of special publications that cover a wide range of cybersecurity topics, including secure configuration management. Publications such as NIST SP 800-128 and SP 800-123 provide guidance on securing information systems through effective configuration control and monitoring.
3- OWASP Application Security Verification Standard (ASVS)
Developed by the Open Web Application Security Project (OWASP), the ASVS is a comprehensive checklist for verifying the security of web applications. While it primarily focuses on application security, it includes a section dedicated to configuration-related controls. This section outlines best practices for securely configuring web application components, such as session management, authentication mechanisms, and security headers.
4- ISO/IEC 27001
ISO/IEC 27001 is an international standard for information security management systems (ISMS). While it covers various aspects of information security, it also includes considerations for secure configurations. Specifically, it emphasizes the need for defining and implementing controls to ensure that information systems and assets are configured securely.
Additionally, following best practices can help in addressing common security misconfiguration habits and their consequences:
- Change defaults: Ensure that system defaults and configurations are updated and set to secure values, minimizing the risk of misconfigurations from the start.
- Follow the principle of least privilege: Grant users and systems only the necessary permissions and privileges to perform their intended tasks, reducing the potential impact of misconfigurations.
- Regularly update and patch: Keep software, frameworks, libraries, and operating systems up to date with the latest security patches and updates to address known vulnerabilities.
- Secure sensitive information: Properly protect sensitive information such as credentials, API keys, and encryption keys by securely storing them and limiting access to authorized personnel.
- Enforce strong access controls: Implement robust authentication and authorization mechanisms, including multi-factor authentication (MFA) and role-based access controls (RBAC), to prevent unauthorized access and limit potential misconfigurations.
- Educate and train personnel: Provide regular security awareness training to employees, emphasizing the importance of secure configurations and the potential risks associated with misconfigurations. Feel free to check out Software Secured’s Developer Security Training.
- Establish change management processes: Implement change management procedures to ensure that configuration changes are properly reviewed, approved, and tested before deployment, minimizing the likelihood of misconfigurations slipping through.
By adhering to these best practices and integrating them into your organization's security processes, you can significantly reduce the likelihood and impact of security misconfigurations, enhancing your overall cybersecurity posture.
Final thoughts
Security misconfigurations are a dangerous threat to systems and its place in the OWASP top 10 for over a decade proves it. These misconfigurations serve as an initial foothold for adversaries to start exploiting your systems. In this article, we touched base upon different aspects – what security misconfigurations are, their impact, common security misconfiguration habits, and how to tackle them. To combat security misconfigurations, we need a multifaceted approach. Conduct regular asset inventories, use automatic detection tools, and employ penetration testing to view things through an attacker's eyes. Don't forget about continuous monitoring and auditing to keep configurations in check.
By following industry best practices and frameworks, we lay the groundwork for secure configurations. Remember, every misconfiguration resolved is a step closer to a more secure future! Looking to get your organization tested for security misconfigurations? Book a call to schedule a pentest. Confident that you’ve taken care of all misconfigurations? Get a one-time pentest and have the satisfaction of being right!




.avif)