Understanding the Difference: External Penetration Testing vs Vulnerability Scanning
The difference between external network penetration testing and vulnerability scanning is significant. Each approach has its own advantages and disadvantages, and knowing when to use each one is crucial.
The world is increasingly embracing digital technology, and hackers are doing the same. Cyber attacks have become common. As businesses expand their online presence, the likelihood of attracting a cyber attack increases. External penetration testing can serve as your protective shield if you want to protect your company from potential harm.
What Is External Penetration Testing?
External network penetration testing is a type of security assessment that focuses on identifying and exploiting vulnerabilities in an organization's externally facing systems and infrastructure, such as websites, email servers, firewalls, and other publicly accessible assets. The goal is to simulate an attack from the perspective of an external adversary who does not have internal access to the organization's network.
What is Vulnerability Scanning?
Vulnerability scanning is an automated process that identifies security weaknesses or vulnerabilities in an organization's systems, networks, applications, or devices. It uses specialized tools to scan for known vulnerabilities, misconfigurations, outdated software, and other potential security issues, providing a detailed report to help organizations address these risks.
What are the Main Differences Between External Network Penetration Testing and Vulnerability Scanning:
1. Purpose
2. Depth of Analysis
3. Methodology
4. Skill Level Required
5. Output
6. Use Cases
How External Penetration Testing is Performed
Conducting an external penetration test involves several key steps:
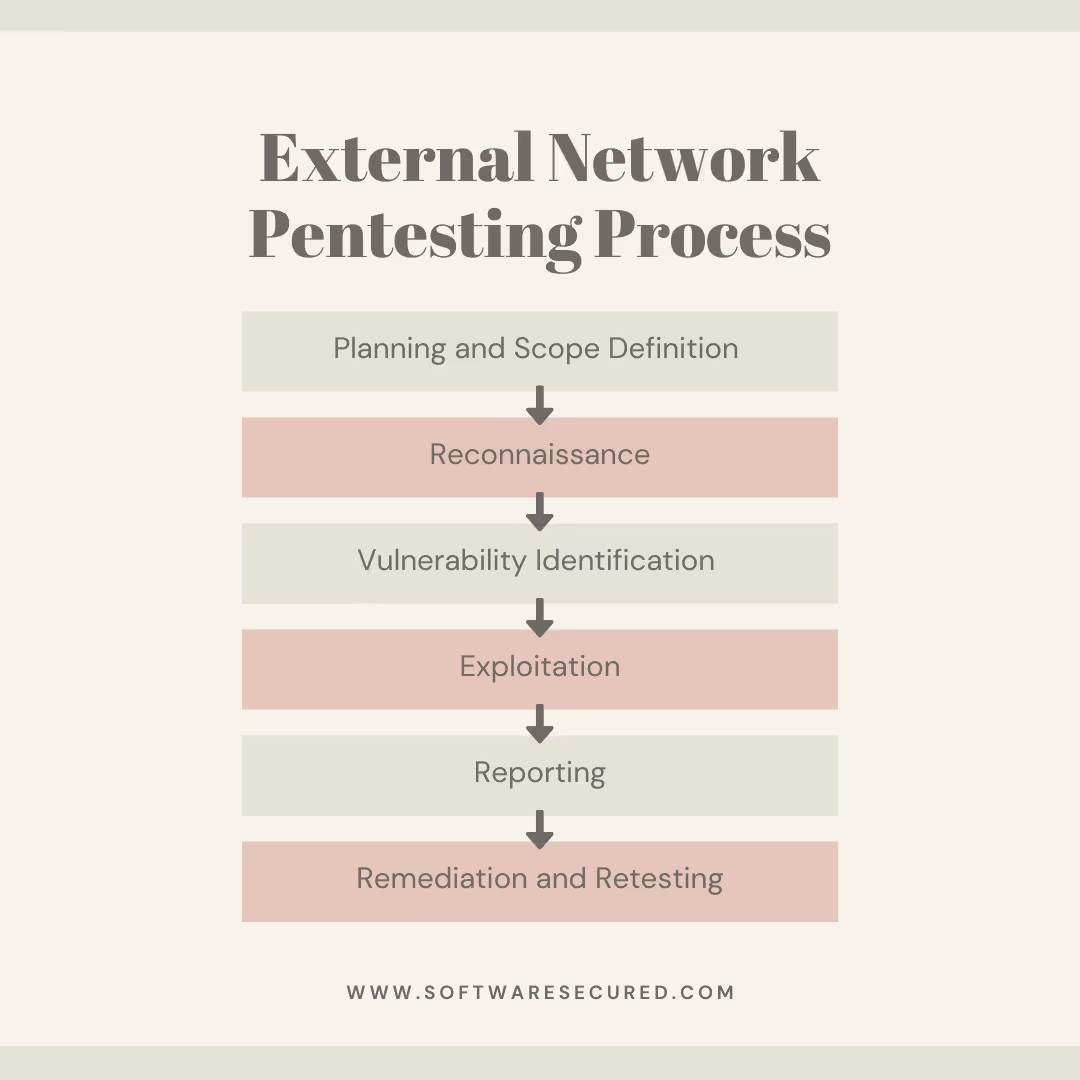
External Network Pentesting Process
How Much Does an External Pen Test Cost?
The cost varies based on factors like the scope of testing, the complexity of your systems, and the expertise required. While an investment is involved, the cost of a breach can be far greater. Investing in penetration testing can save you significant time and money in the long run.
Software Secured's External Network Pentest starts from $5,400, check our prices.
Take the Next Step—don't leave your security to chance. Contact us today to learn how Software Secured can tailor an external penetration testing solution to meet your specific needs. Together, we'll build a robust defence that keeps your business and customers safe.

.avif)
Domain%2520Takeover%2520via%2520EC2%2520IP%2520Takeover.avif)


