20 Cybersecurity Statistics for SMB's
Learn more about the current cybersecurity landscape for SMB's, with insights, trends and recommendations to keep your organization secure.
In today’s digital landscape, data breaches and cyber-attacks continuously sprawl across headlines and reports as the volume of these incidents continues to increase. How do you protect your organization? The hard part is understanding who is at risk, why and when you might fall prey to an attack, how pervasive attacks are and what types of threats are most likely to occur. You must also understand the costs and consequences associated with attacks, measures that prevent a cybersecurity attack, and the fallout once an attack or data breach has occurred. We have put together a list of cybersecurity statistics for small and medium businesses (SMBs) to understand the current cybersecurity insights and findings. Explore these 20 cybersecurity statistics for SMBs to gain valuable insights and stay informed about the current cyber threat landscape.
1. 47% of SMBs have fallen victim to a cyberattack in 2022.
SMBs fall victim to cyberattacks just as often as large corporations, but they often do not have the same resources and infrastructure to prevent, identify and remediate cyberattacks. Although SMBs may not have the same resources as enterprises, there are still ways to prevent phishing and other cyber attack methods.
2. 46% of SMBs have no clue about managing cyber risks.
Despite SMBs being a large target for cyberattacks, many do not have an idea of how to manage their cybersecurity posture or risks. This is important, as SMBs are just as vulnerable as any other large-sized organization, but do not have the same resources and support for cybersecurity efforts. We want to share with you How to Build the Most Effective Organizational Security Strategy.
3. Though 43% of attacks are aimed at SMBs, only 14% of these businesses are prepared to defend themselves.
Using some of the methods explained above, SMBs can prepare themselves using a variety of measures. Some of the most common (and easy) ways to implement additional measures of security are:
- Multi-factor authentication (MFA)
- Password Manager
- Role-based authentication
- Security onboarding/offboarding for employees
- Secure sharing (Send Safely etc.)
Using safer implementations of everyday activities is one small step to helping secure your SMB, and these can make a large difference.
4. 91% percent of all cyber attacks begin with a phishing email to an unexpected victim.
It’s often said that humans are the weakest link when it comes to security operations and safety. Email is one of the best methods through which to get into contact with people in an organization. This means that most security breaches are avoidable if people are trained to spot and avoid phishing emails. Thus, organizations must invest in security awareness training programs for both developers and non-technical roles.
5. Phishing attacks ended up being the most expensive initial attack vector, costing USD 4.91 million.
Phishing is not only the most common attack vector, but it is also the most expensive. Phishing is becoming an extreme threat, as it is one of the easiest ways to initiate a cyberattack for SMBs, but it is also the most costly. Phishing is so profitable and successful, that threat actors are willing to invest money into it to increase the volume of messages and the odds of a successful campaign. This means that dealing with phishing messages becomes financially expensive for organizations. The increase in volume and quality of these emails are making them harder to prevent and can lead to successful attacks.
6. Average time to fix high-severity vulnerabilities grows from 197 days to 246 days in 6 months.
Attackers are becoming more advanced and are shortening the time needed to exploit vulnerabilities, and this continues to get faster every day. The time to identify and fix high-severity vulnerabilities is growing larger, which is all the more reason to invest in preventative measures such as quarterly penetration testing. Quarterly penetration testing allows you to identify and fix vulnerabilities in a smaller window and decreases the chances of the severe vulnerability being exploited.
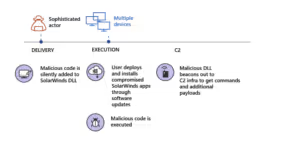
7. Analyst firm Gartner predicted that by 2025, 45% of global organizations will be impacted in some way by a supply chain attack.
Cyber incidents, such as the breach at software management vendor SolarWinds and Log4j in the open source world, put organizations around the globe at risk. In the case of Log4J, the vulnerability was weaponized almost immediately with several variations after each patch. In 2021, Log4J had massive, immediate impacts on companies of all sizes around the world. This trend is something that has already been noticed in 2022, and will only continue to grow in 2023.
8. 50K websites are hacked daily and every 39 seconds, there is an attack on the website.
SMBs often believe they are immune to cyber attacks, but they are often bigger targets than they may realize. Websites all over the world are being attacked daily, including SMBs. SMBs may not have information directly on their website that a threat actor may be looking for, but they may be connected to it.
Island hopping attacks are becoming a large concern for SMBs, as threat actors target an organization’s third-party partners to use them as an access point to the target organization’s network. A recent example includes Toyota Motor Corp., which was forced to suspend its factory operations at 14 plants in Japan after a supplier of plastic parts and electronic components was hacked last February. As a result, the company’s output was cut by nearly 13,000 cars. SMBs are often connected in some way to larger networks and organizations, which allows threat actors to circumvent many of the target company’s defences by exploiting a company that is already trusted by that company and using them to gain access.
9. 18% of websites are infected with critical severity threats.
SMBs need to take proactive measures to protect their websites from cyber threats. Penetration testing can identify vulnerabilities and weaknesses in a website's security. A critical severity vulnerability means that your website is at risk of being hacked at any time. It is recommended in typical service level agreements (SLAs) that you make it your highest priority to fix these vulnerabilities immediately. Even if an SMB feels that they are secure, penetration testing can provide valuable insights into their website's security posture and help them address any potential issues before they can be exploited by attackers.
10. Software Secured saw a 133% increase in DoS and DDoS attacks compared to the previous year.
In our State of Penetration Testing as a Service Report, we found Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks increased by 133% compared to last year. The UK finance sector also saw a 4% increase in DDoS attacks compared to last year.

The ease with which DoS attacks can be coordinated has meant that they have become one of the most pervasive cybersecurity threats that modern organizations have to face. DoS attacks are simple but effective and can bring about devastating damage to the companies or individuals they are aimed at. With one attack, an organization can be put out of action for days or even weeks.
11. Security Report found that ethical hackers were able to discover over 65,000 vulnerabilities in 2022 alone, up by 21% over 2021.
More websites are infected than you realize, and it is more likely your site is vulnerable in one way or another. The digital landscape and connectivity are continuing to expand between applications and vendors, creating a larger attack surface where vulnerabilities become more common. The lack of developer secure code training is another reason for the increase in vulnerabilities. More applications are being released every day, as we continue to rely on these applications for vendor/customer/business needs. Without proper security training, and regular code reviews for vulnerabilities, it is very easy to introduce vulnerabilities into an application.
Want to learn more about leading security-minded developers? Read 4 Practices to Leading Security-Minded Developers!
12. Data breaches lead to an average of $4.24 million in damages.
The average cost of data breaches varies significantly across different industries. The healthcare industry has the highest average cost at over $9 million. On the opposite end of the spectrum, public sector data breaches average just under $2 million in damages.
Although the average costs of data breaches vary from industry to industry, the fines are becoming increasingly larger year over year. It is imperative that companies not only consider, but prioritize security measures to avoid damages, and other significant costs that come with data breaches.
13. American companies suffer the greatest financial losses from data breaches.
The average cost of a data breach for US-based companies is $9 million. Companies in the Middle East pay an average of just under $7 million per data breach, while Canadian companies average $5 million in damages.
14. 62% of data breaches lead to C-level executives’ resignations or termination.
Data breaches are often met with swift consequences within American companies. 40% of breaches led to legal issues, 38% to staff terminations, 27% to reputation damage, and 16% to financial losses.
Not only are data breaches damaging to your customer base, but they are also damaging to your executive board. In 2023, the importance of C-level executives being involved in cybersecurity strategy is greater than ever. Data breaches are no longer just a technical concern, they are a business concern. Want to learn more about the reasoning behind the strategy shift?
Read 4 ways security leaders uses penetration testing to elevate their security programs
15. Data loss and data privacy are the biggest concerns among cloud security professionals.
Over 60% of cloud security professionals reported that both data loss and data privacy were major concerns. Over 40% reported concerns about accidental credential exposure, regulations, compliance, transparency, and visibility.
We have learned that data privacy and security are a large concern for B2B technology buyers, but cloud security professionals are just as concerned. Cloud security professionals understand that security not only affects buying technology or a data breach but all of the other exposures, dangers and damages that come along with data loss and privacy breaches.
16. 65% of B2B technology buyers say data security and data privacy are top considerations when purchasing new tech.
As cyber-attacks and data breaches become more prevalent, businesses are becoming more cautious about the technology they invest in. This trend has led to an increased demand for tech products and services that can prove compliance or proof of their security through penetration testing. Data breaches can affect not only the buyer but also their customers, potentially compromising their personal information and damaging their trust in the company.
Penetration testing is an effective way to identify vulnerabilities and prevent cyber-attacks, making it an essential tool for SMBs that want to protect their data and maintain their vendors/customers' trust. Penetration testing also helps vendors meet compliance requirements, which can help organizations prove their data security and privacy via compliance certifications.
17. Of the 1,134 B2B tech buyers surveyed by Trust Radius, 3 out of 4 said that security concerns led them to do extra product research before taking any further action. Over a quarter said that security concerns led them to consider fewer products.
Many vendors are investing in technologies like encryption, multi-factor authentication, and network security to ensure that their products are secure, and they are starting to require their vendors to do the same.
More vendors are obtaining security compliance certifications, such as SOC 2 and ISO 27001, to provide independent validation of their security controls and give their customers added assurance.
18. Health Insurance Portability and Accountability Act (HIPAA) compliance regulations impact 79% of North American Managed Service Providers (MSPs).
HIPAA compliance is currently the biggest challenge for MSPs in the US, Canada and Puerto Rico. In Europe, the Middle East, and Africa, MSPs are most impacted by GDPR compliance regulations.
19. Healthcare remains the top target of ransomware attacks.
Compliance requirements are growing, especially in sectors where HIPAA is remotely in play. The healthcare industry contains some of the most sensitive customer information, and companies are becoming increasingly concerned about data breaches with sensitive patient information. HIPAA is no longer a “nice-to-have”, it is now a pretty strict requirement.
20. Amazon Europe’s €746 million fine was the largest GDPR violations fine in history.
The EU is known for having the strictest data privacy compliance regulations, and Amazon got hit with the EU’s largest fine to date in July of 2021. The €746 million fine was over three times larger than the next-largest fine — Whatsapp Ireland’s €225 million fine in September 2021.



.avif)

