SOC 2 Report Explained: What It Is and Why Customers Demand It
Discover why enterprise customers request SOC 2 reports. This guide explains requirements, benefits, and how to prepare your company for faster client trust.
Audit types
Before diving into the SOC framework, it is important to understand the three different types of audits your company can perform:
- Internal: Ran internally by your team, it is put in place to measure and control internal standards and processes.
- External second: Ran by another company such as a client to ensure that your company is meeting the requirements specified in the contract.
- External Third-Party: Ran by an independent auditing company to validate that your company is conforming to a set of standards, such as the SOC standards.
Third-party audits allow you to distribute a report as well as display a logo on your website, proving to your existing and potential clients that you have been audited and have passed said industry standards.
Understanding the Difference Between SOC 1 and SOC 2 Reports, Type 1 and Type 2
"The SOC standard is updated regularly to adjust to the fast-moving industry."
Who is Responsible for SOC 2?
The American Institute of CPAs (AICPA) is in charge of designing and maintaining the SOC framework. It is updated regularly to adjust to the fast-moving industry.
Exploring the SOC Framework and Its Importance
SOC, which stands for Service Organization Control, is a reporting framework. The reports compiled by the auditing company are the ones you will be distributing to your clients and are the result of auditing standards followed by the auditors.
Key Contrasts Between SOC 1 and SOC 2 Reports
Both SOC 1 and SOC 2 audits exist to validate the controls in place at your company and let your clients know that you are following industry standards.
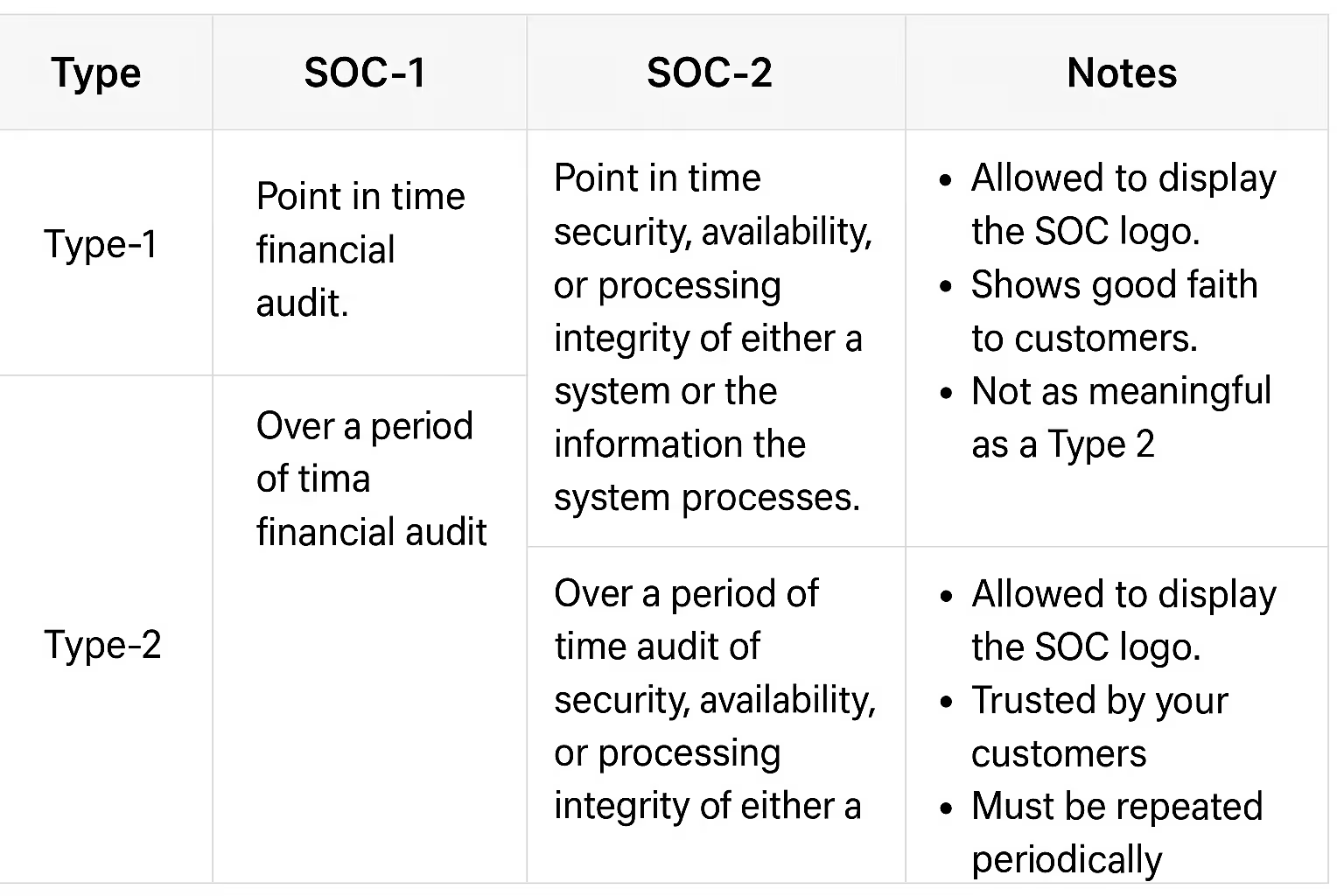
SOC 1 is used to audit the controls relevant to your company’s finances.
SOC 2 is used to audit the controls relevant to the security, availability, or processing integrity of either a system you are running or the information the system processes.
Differentiating Type 1 and Type 2 SOC Reports
Both SOC 1 and SOC 2 exist in two flavours:
Type 1: A point-in-time audit, during which auditors evaluate and report on the design of controls your company put into place as of a point in time. This is a great way to show good faith to your customers.
"This is how you show your clients and customers that you are continuously following industry standards."
Type 2: Happens over a period of time. This type of audit follows a Type-1 audit and is what larger prospects will be after. Auditors usually recommend a 6-month period for the first audit and 12 months for consequent audits. It is important to note that there are no requirements or standards for the audit duration other than a 3 months minimum period.
At the end of the period, auditors will review the controls you put in place during the Type-1 audit, except this time auditors will ask for historical data. This is how you show your clients and customers that you are continuously following industry standards.
As an example, let’s assume that you have a procedure in place to revoke access to a terminated employee:
- During a Type 1 audit, auditors will review this policy and make sure it conforms to the SOC 2 reporting standard.
-During a Type 2 audit, the auditors will ask you for a list of all employees who left during the Type 2 Period months period and will be looking at proof that you followed the policy in place. This also includes performing a penetration test.
Determining If You Need a SOC 2 Report for Your Business
If your company offers a SaaS solution, a SOC 2 report will prove to your clients that you are handling their data safely by following trusted industry standards. It will make the difference between you and your competitors. Starting with a SOC 2 Type 1 report is a great first step to understanding the technicalities of the audit before moving to the SOC 2 Type 2 cycle. Understanding what a SOC 2 report is and why your clients are asking for it can help you navigate the audit process more effectively.



.avif)

