How to Overcome the Biggest Barriers to Selling Security Internally
Learn about overcoming the biggest barriers to selling security internally, and how penetration testing can help overcome these barriers.
71% of organizations worldwide became victims of ransomware at least once in 2022. Cybersecurity threats are becoming increasingly sophisticated and frequent, making it more critical than ever for organizations to protect their sensitive data and assets. Alongside ransomware, insecure coding practices are a large risk for organizations, and this is where penetration testing can help discover and remediate vulnerabilities from the ground up.
Despite the critical role that security plays in an organization's overall growth and resilience, there are several challenges that security professionals face when trying to sell security internally. The four most significant barriers are…
- Lack of awareness
- Budget constraints
- Resistance to change.
- Competing priorities
We will uncover why these barriers exist, and how to overcome them to close enterprise deals, increase the ROI of security investment, and improve your overall security posture. We will also dive into how penetration testing as a security investment can help overcome these internal barriers, and how it can improve your overall security program maturity.
The biggest barriers to selling security internally
Let’s dive into the biggest barriers to selling security internally, the reasoning behind these barriers and how to overcome them.
Lack of awareness
One of the most significant barriers to selling security internally is the lack of awareness about the importance of security among stakeholders. Many decision-makers in organizations do not fully understand the potential consequences of a cyber-attack, such as financial losses, damage to reputation, and legal liabilities. As a result, they may not prioritize security, leading to a lack of investment in internal security measures. On average, Canadian companies are paying $2 million dollars in remediation per cyberattack. On the flip side, organizations that adopt a strong cybersecurity network architecture by 2023 will reduce the financial costs of data breaches by an average of 90%.
Here are some reasons why cybersecurity lacks general awareness:
No security education
Security leaders, developers, and other decision-makers may not fully understand the importance of cybersecurity and the potential risks associated with not following security policies and procedures. Forrester looked at the top 40 computer science programs and found that “None of the top-ranked computer science programs in the United States require a class about secure coding or secure application design.” In most instances, general cybersecurity courses are offered as an option rather than as a priority in many schools. This means that proactive secure coding practices are not taught to developers from the foundation, and require education beyond their initial degree.
Confidence in Current Cybersecurity Efforts
Your organization may feel that its current security measures are sufficient and may not see the need for additional measures. For example, you may do a penetration test or vulnerability scan once a year, and have various security measures already in place.
However, it is essential to stay up-to-date with the latest security best practices organization-wide, as well as continuous updates to your application system. Frequently updating and improving your security measures helps keep pace with evolving threats. Conducting quarterly penetration testing can help organizations meet the expectations of their stakeholders, including customers, investors, and employees. Customers, in particular, are increasingly concerned about the security of their data and are more likely to do business with companies that can demonstrate their commitment to data privacy and security. You may have adequate security, but is it enough to protect your organization and your customers?
Overcoming lack of awareness
To overcome these challenges, security leaders must take proactive steps to raise awareness about cybersecurity among their internal teams.
Some effective strategies include:
- Tailored and frequent training:
- Security leaders can develop training programs tailored to different departments or roles within the organization. This can help employees better understand how security measures directly impact their work and why they are necessary.
- Getting leadership buy-in:
- Security leaders can enlist the support of senior executives and other leaders within the organization to reinforce the importance of security.
- By 2025, 70% of CEOs will mandate a culture of cybersecurity-focused awareness and resilience. This can help build a culture of security and promote a sense of responsibility and ownership among employees.
- Unless management understands the value of security and supports efforts through things like training and continuous education.
- Without leadership buy-in, then any additional efforts to improve the security practices of the organization are unlikely to gain any traction.
- Developers and the security teams should work together towards common goals, and develop ways of integrating security into the SDLC in a way that works for both parties.
- This will take time, effort and collaboration from both ends to mature your security program.
Budget constraints
Budget constraints are another significant barrier to selling security internally. Companies usually spend between 7-10% of their IT budgets on security requirements. The return on investment (ROI) of security investments like penetration testing is easy to prove, but hard to quantify with tangible and impactful metrics. There are various ways to communicate the value of security investments, and different aspects will speak to different values in your various organizational departments. The IT or security team will have different measures of ROI than CFO’s or CEO’s. It is important to understand these differences and provide metrics that are valuable to both parties involved in security strategy decisions. When the CFO and CTO work together, organizations are better able to allocate resources and make strategic decisions to improve their cybersecurity posture.
There are 2 impactful metrics you can use to help overcome barriers to selling security internally:
- ROI of proactive cybersecurity measures
- Cost of avoided risk (regulatory fines)
Looking for more metrics to help track your ROI and progress of security investment over time? Read Penetration Testing ROI: 5 Metrics to Communicate Real Value!
ROI of proactive cybersecurity measures
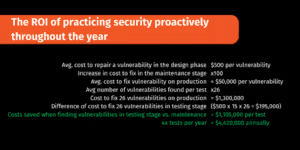
One way to prove the worthwhile investment in security is through the ROI of security investments. For example, the figure above shows practicing security proactively via penetration testing throughout the year provides a large ROI for an organization.
For example, the cost to fix a vulnerability in the production phase is 100 times more costly than fixing a vulnerability in the design phase. This means the average cost of $500.00 to repair a vulnerability in the design stage is multiplied by 100. On average, Software Secured finds 26 vulnerabilities per test. The average cost saved when finding vulnerabilities in testing staging versus maintenance is over 1 million dollars per test. If an organization does quarterly tests, it can save over 4.4 million dollars annually. When calculating the ROI, try to do your estimate for the expected returns in 3 months, 6 months, and 1 year.
Once a penetration test report is delivered, your developers might choose to spend additional time learning about vulnerabilities, remediating patches, and reaching out to the penetration testing team for support. As your team continues to integrate and shift left with their development practices, you will see benefits and returns in numerous areas.
Forrester Research found an ROI of 205% over three years, with a real dollar return of almost $7 million on a $3.3 million investment when companies began to shift left with their security automation. These benefits from shift-left automation included increased output per developer, decreased testing time, improved risk avoidance and bug remediation. In the Forrester Study, the tools studied removed about 20% of the bugs from the software which aligns with the direct cost avoidance savings. Although the additional overhead and resources may be a large reason for resistance to change, the additional benefits to your security program outweigh the additional efforts in the beginning.

Potential regulatory fines
How much can you expect to pay for a security incident? Each regulatory body has specific jurisdiction and authority to enforce data breach fines. 60% of small businesses go out of business within 6 months of a data breach. Several regulatory bodies enforce data breach fines, and it is crucial to know which regulatory body applies to your organization.
Here is an overview of the fines imposed by various regulatory bodies:
PIPEDA
At this time, businesses and organizations can be fined up to $100,000 CAD for each violation. While the fine might not be invoked for every PIPEDA violation, OPC is aggressive in its investigations.
GDPR
The GDPR, which applies to organizations that process personal data of EU citizens, imposes fines of up to 4% of a company's global annual revenue or €20 million, whichever is greater.
CCPA
The CCPA, which applies to businesses that collect personal data of California residents, allows for fines of up to $7,500 per violation.
HIPAA
HIPAA, which regulates the handling of PHI, can impose fines of up to $1.5 million per year for violations.
FTC
The FTC may bring civil actions for civil monetary penalties of up to $40,000 per violation of the FTC Act or COPPA. Each day that non-compliance continues is considered a separate "violation" for purposes of the law.
PCI DSS
The payment brands may fine an acquiring bank $5,000 to $100,000 per month for PCI compliance violations. Furthermore, the bank will also most likely either terminate your relationship or increase transaction fees. Penalties are not openly discussed nor widely publicized, but they can be catastrophic to a small business.
Understanding both the potential ROI of security investments and the financial repercussions of data breaches from regulatory bodies can help convey the importance of investing in maturing your security program. Using figures, metrics, and any documentation can help visualize the benefits for all departments and parties involved. The more data and support you have, the easier it will be to overcome the barrier of budget constraints for selling internally.
Resistance to change
Finally, resistance to change is another significant barrier to selling security internally. Your organization may be reluctant to implement new security measures due to conflicting internal goals, and the mindset shift required when it comes to DevSecOps.
Security conflicts with other internal goals
In the agile framework, with stricter timelines and bigger pushes for faster features, there is often not as much time to complete adequate security testing. 52% of organizations report sacrificing cybersecurity for speed-to-market. Prioritizing growth over security can be a large barrier to selling security internally, as security is often seen as a roadblock to fast growth.
Developers and security teams are known for having turbulent relationships, as they often do not see eye to eye for internal goals for new applications or products. This is no fault or blame for either team. Developers want to move quickly, shipping out products and features fast for their customers, and using automation and continuous improvement to do it. This is less of a priority for security. Rather than move fast, security teams are there to ensure that code goes out safely, without introducing any unexpected vulnerabilities to their systems. This contrast is at the source of many of the issues that lie between these teams — especially since they have often worked in silos to create processes, goals, and performance indicators that align with their worldviews.
So, how do you shift both teams' mindsets for a more efficient and collaborative department? We have 5 best practices for shifting these mindsets to ensure improved communication.
Building a shared responsibility for security
Equipping developers with cybersecurity knowledge can go a long way to fostering alignment. Some companies offer security boot camps and learning sessions that developers can partake in for this purpose. The same goes for security, there can be various training to help understand the development process and where they can best see security integrations fitting. Once both teams have an understanding surrounding the other team's processes, goals and habits you can begin to build a shared responsibility for security.
Developers are accountable for the code they produce and how it functions, and many believe that security should be part of that purview. Where the security team can help here by ensuring that the developers have the tools and any automation they need to write secure code easily and fast. The security team also has the important role of assessing risk and communicating what developers need to do to mitigate that risk. This shared responsibility can help drive balance between both teams, setting them both up for success as they work towards the same goals.
Expanding observability
Dev and sec teams with robust observability platforms can view system health and security from anywhere. This gives them the ability to access context and analysis in real-time so that they can act quickly and with precision when an issue arises. For example, when a security breach happens, both dev and security teams are alerted with the appropriate data, allowing them to collaborate on a solution. In the event of a system outage, devs can focus on bringing things back online while the security team reinforces policies and covers any potential vulnerabilities enhanced by the outage.
Setting policies that account for both teams
Security standards have become a big part of how we view and treat security, but they only gain real traction once security teams turn them into actionable policies that can be incorporated into workflows. This is where it can be useful to extend the spirit of collaboration and invite developers to the table. This way, they can contribute insights into what will be easy to adopt, where automation could help, and what information might be lacking for the dev team to make the policy fully actionable.
In addition, this approach can make it easier to set expectations around a given security process and identify what team is responsible for each step.
As a bonus, bringing the dev team to the table can also remove the need for security team members to be enforcers, a role that sometimes leads to antagonistic conversations with devs.
Encouraging mutual empathy, understanding, and feedback
This one feels like common sense, but it’s still worth talking about. Security professionals and devs have arrived at their roles through different paths, prioritizing different results, so there’s often a need for sharing these perspectives and experiences.
A few ways to encourage mutual understanding are through roundtable events where individuals can share their security or development challenges, casual gatherings, buddy systems, or having the two teams work in proximity to each other.
Ensuring transparency on decisions and progress
Communication between security and dev teams should be transparent and abundant — one team should rarely (if ever) be surprised by the other. Beyond consistent messages, which can be automated where possible, this can also look like hosting sprint planning meetings together, and gathering to review security reports once they’re delivered to come to a consensus on how to move forward.
As a result, you’ll be able to:
- Maintain trust between teams
- Guarantee visibility across the board
- Facilitate ongoing collaboration
- Uphold the culture of security you’ve built
How penetration testing can help overcome these challenges
Penetration testing can be a powerful tool for overcoming the biggest barriers to selling security internally. By providing a realistic assessment of an organization's security posture, penetration testing can help create awareness about the importance of security and prove the ROI of the investment towards maturing your security program.
Creating awareness
Penetration testing can help create awareness among non-technical stakeholders about the potential consequences of a cyber-attack. Penetration testing can provide detailed reports on how vulnerabilities are created which helps the developers do better going forward. Reputable penetration testing vendor reports should provide you with clear results.
The penetration test report should be…
- Comprehensive
- Actionable
- Easy-to-follow
- Includes steps to reproducibility
- Checked by various team members to ensure 0 false positives
- Prioritizes vulnerabilities based on severity
Penetration testing is a great way to understand what could happen to your application if an unethical hacker were to exploit a vulnerability in your application or system, and what kind of real-world damage they could potentially do. Using these metrics can help prove the importance of security investments.
Proving ROI
Penetration testing results can be used to prove the return on investment, as seen above by providing concrete evidence of the potential risks an organization faces. By demonstrating how vulnerabilities can be exploited and the potential consequences of a successful attack, penetration testing results can help decision-makers understand the importance of investing in security measures.
Here are 3 ways to prove ROI with penetration testing efforts:
Threat modelling to extend coverage
While penetration testing at an organizational level communicates that it is taking the necessary measures to ensure the safety of its data, the addition of a threat model will only magnify the strength.
The detection of initial threats and potential attack points paves the way for a penetration test.
Threat modelling can add value to a penetration test in several ways:
- It can help penetration testers identify the most critical areas to test by prioritizing potential threats and vulnerabilities based on their severity and likelihood of occurrence.
- By identifying the most critical threats and vulnerabilities, threat modelling can help organizations prioritize their remediation efforts to address the most significant risks first.
- It forces both the penetration testing team and the organization to think about all kinds of threats and vulnerabilities that may be present in the system or application.
- Threat modelling can help identify blind spots in the testing process and reveal social engineering or other threat possibilities that aren’t necessarily tied to the scope of the penetration test.
- A proper threat modelling session can help organizations understand the business risks in more quantitative terms. It also gives organizations a better idea of their assets and the risks associated with them. This improves the overall outcome of security testing.
Using a penetration testing vendor that conducts threat modelling not only adds additional value to your coverage but also helps provide business context for various stakeholders.
Align penetration testing efforts to compliance
By aligning your compliance efforts with penetration testing, you can ensure security coverage and prove your commitment to data privacy to vendors and customers. Compliance and penetration testing help close enterprise vendor deals that require compliance, such as SOC 2, ISO27001 and more. By combining compliance and penetration testing efforts, your team can:
- Avoid false positives
- Prove your security posture to your auditor faster
- Reduce your cybersecurity insurance costs
Learn How Penetration Testing Increases Your ROI of ISO 27001 Compliance here!
Highlight business requirements
Highlighting business requirements alongside the technical requirements will ensure an organization-wide understanding of the importance of security. In recent years, penetration testing has shifted to become more of a business requirement than a technical requirement - for various reasons. The four main reasons are
- Regulatory compliance
- Risk management
- Competitive advantage
- Cost-effectiveness.
Now more than ever, C-suite executives are urged to become more involved in security measures due to the climb in data breaches. “48.8% of C-suite and other executives expect the number and size of cyber events targeting their organizations' accounting and financial data to increase in the year ahead.” C-suite executives and other leaders are becoming increasingly aware of their need to be involved in preventing data breaches, and by understanding these needs and shifts you can speak to specific business requirements that benefit from penetration testing. Highlighting how penetration testing can solve business risks helps further prove penetration testing ROI, and can help break those barriers into selling security internally.
Conclusion
So, how can we make security a priority for everyone in our organization? The answer lies in developing a clear and concise message that resonates with all stakeholders, demonstrating the importance of investing in security measures, and providing concrete examples of the benefits and ROI. Overcoming these barriers is possible if you can align the security goals with the goals of all internal stakeholders and convey metrics/data that are relevant to their roles and objectives. Conducting penetration testing can be an effective way to convince upper-level management to invest in security, as it provides realistic outcomes of potential damages and consequences. We encourage security leaders to build data-driven cases on how integrating security is a crucial step to growth and resilience, not a hindrance. Talk to our team to learn more about how penetration testing can help your team overcome these big barriers to selling security internally.




.avif)