How a Pre-assessment Checklist Helps With Preparing for a Penetration Test
Learn more about penetration test pre-assessment checklists and how these checklists helps prepare your organization for a penetration test.
What is a penetration test pre-assessment checklist?
Whenever a company is planning on doing a penetration test, we require them to prepare a pre-assessment checklist. This list of items helps to ensure that the penetration test returns information that will help the business meet its objectives, and remain on the same page as the client such as scope. Let’s look at what this checklist should include:
Details the pentesters need to know: The first element of the list should be a list of questions that outline a few details our pentesters need to know to prepare for a penetration test. For example, the pentesters may want to know if you’re looking to meet a certain compliance regulation, if you’re looking to meet a certain security standard or if you’re worried about a specific set of cyber attacks etc. Questions related to your business objectives should be included in the checklist. This way the pentesters can focus their efforts on the security gaps that you are most concerned about.
Provide information about the application: You should be asked to provide information/context about the application that will be tested. This should include things like which frameworks were used in making your app, the cloud hosting platform, the type of databases it uses, the type of API platforms and how many endpoints there are that need to be tested. Providing this information allows the testers to be more targeted in their approach and ensure that all elements of your environment are properly examined.
By providing this information upfront you remove any blockers that may delay the penetration test or negatively impact the effectiveness of the test. This information also helps guide how prepared someone is for a penetration test and the amount of work that needs to be done before the penetration test can begin. Lastly, it helps the tester prepare questions for future meetings to ensure they understand the full scope of the engagements. For example, they may want to request an application demo.
Importance of Consent, Legal Compliance, and Collaboration in Preparing for a Penetration Test
Obtaining consent and ensuring legal compliance are crucial steps in preparing for a penetration test. Before initiating the test, it's essential to discuss and agree on the specific type of pentest (black-, gray-, or white box) that best meets the company's needs. Once decided, gather and share relevant documentation with the pentesting team, including walkthrough videos, process diagrams, data flow charts, user role explanations, and access control matrices. This information helps testers conduct a more thorough assessment. Additionally, obtaining consent from stakeholders and verifying that the test won't violate any laws or regulations is vital to avoid legal issues. Collaboration with pentesters throughout the process ensures a well-prepared environment and maximizes the effectiveness of the penetration test.
What does a good penetration test pre-assessment checklist look like?
1- The Application
- Every checklist needs to be asking the client about the nature of the application, in as much detail as possible. The effectiveness of a penetration test will be affected by how well the testers understand the application, its function and its purpose. If they are not asking about your application before the penetration test, this is a red flag.
- It is important to have a demo meeting booked so that the pentesters can see the application live, with all primary use cases to help improve test coverage. Understanding how the application is normally used gives the testers an idea of what the potential attack surface is for the application and what security controls are most important for its function.
- A good checklist will gather all necessary/applicable URLs and IPs for the environment that will be tested. This ensures that all areas of your application are included in the scope of the project and nothing goes overlooked.
- You should determine if a VPN should be used and the specific details required for connecting to the environment. Depending on the structure of the environment the use of a VPN may be required and this should be provisioned before the test to ensure that there are no delays.
- The checklist needs to address the QA/Testing/Staging env. It needs to address what these environments look like and how they are configured. Is there a crossover with any prod elements and can those prod elements be tested as part of the project?
- Do you have a SOC team monitoring the application? If so, they need to be notified of the penetration test to ensure they do not block the testers or otherwise interfere with the engagement.
- Where is the application hosted? Some hosting providers may require authorization before performing a penetration test on their infrastructure and hosting applications. To avoid issues it’s best to address this upfront. You won't require authorization if you are hosted on AWS, Azure or Google.
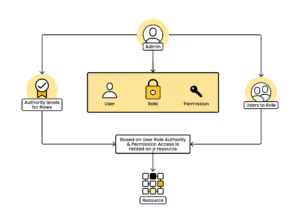
2- User Roles
Another important detail for the checklist is to outline the nature of the roles within your application. The testers will want to know what roles are being used and get a full list of working accounts per application role. For example admin accounts vs normal users vs guest accounts. Account compromise is an important part of a penetration test and by listing all of the accounts you help the testers understand the potential risk, and test for access control issues and privilege misconfigurations associated with each account.
3- Post checklist: What do you need to prepare before your test?
After completing the checklist, there may be remaining action items that you need to do before a penetration test. The penetration test team should advise you on these action items, but here are the most common things people need to prepare for their penetration test.
- Creating a suitable environment: To prevent potential business outages and disruptions we highly recommend clients to test only on staging environments. For those clients that do not have a staging environment, you will most likely need to build one for the penetration test. Additionally, If you have a shared staging environment that is actively used by your dev team. This is a problem because pentesters will pollute everything they touch and make it unusable to their dev team. This can cause delays on their side. There may need to be a prep to divide these environments to ensure that there are no business disruptions.
- Evaluate your application’s traffic threshold: You may need to chat with multiple teams to make sure your application can handle the strength of a penetration test. Many applications are not prepared for the stress the pentesters will place on their system. The stress can be the amount of traffic or the disruptiveness of testing etc.Therefore you need to work internally to ensure that the application is suitable for the penetration test beforehand.
- Ensure the application is complete in the staging environment: If the application has a lot of features like internal plugins etc, they all need to be working in the staging environment, which is rarely the case. If some features are missing then the test will be incomplete and yield incomplete results.
- Ensure the environment is up and running: This is fairly basic but still needs to be said. To prevent downtime, delays and ultimately wasted money and time for the client it’s imperative to have the testing environment be ready and available for the penetration test. Failure to do so can result in fewer vulnerabilities being detected due to lost time.
Conclusion
Pre-assessment checklists help to ensure that penetration testers are thorough in their approach and cover all bases. By having a checklist to refer to, penetration testers can minimize the risk of overlooking something important and ensure that their report provides the most possible value to their clients. Understanding how a pre-assessment checklist helps with preparing for a penetration test is crucial for thorough and effective testing. This not only helps the pentesters focus efforts on higher priority threat potentials, and this can improve the ROI of your penetration test in the long run.



.avif)
