7 Steps to Comprehensive Penetration Testing
We follow an comprehensive pentesting approach, combining the latest hacking techniques manually executed by our experienced engineers.
What’s a Comprehensive Penetration Testing Approach?
The term ‘security assessment’ is used to describe the process of assessing a system, such as a network or an application, to find security flaws that can lead to cyber-attacks. There are several ways to perform security assessments for a system. At Software Secured, we follow a comprehensive penetration testing approach, combining the latest hacking techniques, which are manually executed by our experienced engineers. In addition, we apply our proprietary testing stack, advanced threat modelling, and real-time portal dashboard for reporting, giving you the best coverage and depth in the industry.
Conducting Vulnerability Assessment in Penetration Testing: Techniques and Tools
Vulnerability assessment involves analyzing threat sources and identifying targets to map potential attack vectors. Penetration testers use various techniques to probe the target network, uncovering vulnerabilities such as open authentication access, directory structures, and remote-code execution possibilities. The process often includes DNS interrogation, InterNIC queries, and network sniffing to gather hostnames and IP information. Automated and manual vulnerability scans are conducted to test systems against known vulnerabilities and discover new ones. Testers may utilize resources like the National Vulnerability Database and tools such as Tenable, Rapid7, and Nmap. They also assess high-value assets, including employee and customer data, technical information, and internal and external threats. Web application attacks, such as cross-site scripting and SQL injection, are employed to exploit vulnerabilities and escalate privileges.
Three Factors We Focus on Optimizing
1. Coverage
We use several techniques in our approach to automate the discovery of basic attacks. We continue pushing the boundaries of what tools are capable of finding, giving us the chance to spend more manual testing time on finding harder-to-discover vulnerabilities, such as business logic vulnerabilities. Quarterly deep assessments to locate vulnerabilities and continuous re-testing on patched issues ensure that the application is covered year-round, both during and between major releases.
2. Depth
We follow a stringent process, combined with a checklist of over 200 security items that are reviewed in every assessment. Our checklist is continuously updated with the most recent techniques to ensure that as many code paths in the application have been tested. Better yet, our pentesters apply their creativity and intuition to go deeper, finding new vulnerabilities beyond the checklist, and creating a truly comprehensive test.
3. Comprehensive testing
We spend a fair amount of time understanding the business purpose of the application through threat modelling, allowing us to go deeper and understand the attacker’s motivation. By assessing various use cases, we unlock insights into potential vulnerabilities in the application design that would otherwise remain hidden.
Our Seven-Step Assessment Process
Given our three areas of focus, we follow a seven-step process with every assessment:
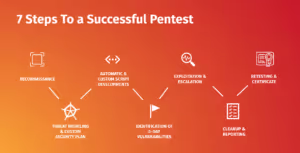
1. Reconnaissance
This stage is all about understanding the application and its unique business logic. Meetings with the client and pen test provider help ensure that all parties are well-informed about the test. The test environment must be ready at this point.
2. Threat Modeling & Custom Security Test Plan
Building out a threat model is essential to understand the common use cases of the application. An effective threat model can also identify security risks in the design of the application, which may be difficult to change at a later stage. However, understanding these risks early helps prepare the rest of the security plan to work around them.
3. Development of Custom Scripts to Assist with Testing
The fun begins. Pen testers start diving deep into the application with a mix of manual and automated approaches.
4. Identification of Zero-Day Vulnerabilities
As critical vulnerabilities are identified, the client is notified immediately. Steps to reproduce the issue are shared with the client so that their development team can begin remediation as soon as possible.
5. Exploitation & Escalation
The less severe vulnerabilities found during the early stages of the pen test are exploited and escalated as much as possible without affecting the function of the application (for instance, if a pen tester is testing a vulnerability and it risks taking down the entire application, they’ll take it as far as possible without creating any actual harm). Test environments and test accounts are created to prevent any real damage and exploitation of the live application.
6. Cleanup & Reporting
Upon completion, pen testers will gather all found issues, regardless of severity, into a report. A good penetration testing provider should also include steps for replicating the issue so that the client’s development team can mitigate the issue.
7. Retesting & Certification
After the report is delivered, the client may patch several vulnerabilities. A quality pen test provider will be able to retest these known vulnerabilities shortly after to verify that they have been fixed correctly or sufficiently. In some cases, the pen tester may require that the client develops a complete fix, and in other cases, a “band-aid” solution may suffice for critical issues that need deeper attention later.
When all is good to go, the pen test provider can offer a certificate to the client as proof of application security. This certification is essential when earning compliance, such as SOC 2 or ISO 27500. It’s also helpful for closing enterprise deals (learn more about vendor security questionnaires here) or for startups that want to generate higher investor appeal.
Conclusion
Our comprehensive penetration testing approach to security assessment can be delivered as a one-off engagement or continuously managed. Discover the 7 steps to comprehensive penetration testing for ensuring robust application security.





.avif)